Keeping You and Your Accounts Safe
Keeping You and Your Accounts Safe
It’s now 2024 and no account is safe. Passwords are becoming less and less secure even though you meet the requirements of the site. Uppercase, lowercase, number, special character and a minimum of 8 characters being the standard still isn’t enough. This is due to all the data breaches from many companies. Compound this with many users using the same password across many services and sites. We will discuss how you can keep your accounts and services safe from most forms of breaches.
Passwords Are The Way of The Past
Passwords are becoming less and less secure. You may be increasing the character count from 8 to 12 or adding in a couple special characters but that still doesn’t make much of a difference. Hackers are aggregating all this data and using it in attacks. ‘RockYou’ is one of the most famous password lists put together comprising of over 14 million passwords aggregated from data breaches. Now with A.I., it’s become even easier for passwords to be cracked.
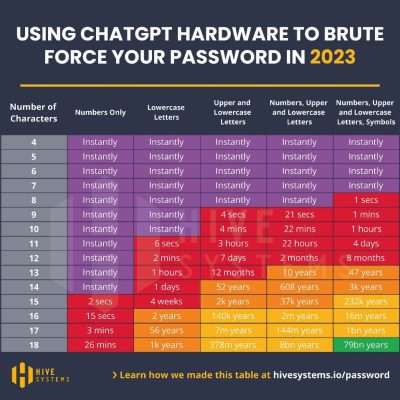
So, What Can I Do?
Utilizing 2FA (Two Factor Authentication) or MFA (Multi-Factor Authentication) is the most popular and effective way to help prevent a breached password from being used against you. Rotating passwords or updating them every so often will help thwart hackers. Make sure the wireless networks you connect to are secure. When on unsecured networks, use a VPN, and always have a good antivirus package or EDR (Endpoint Detection & Response) to protect your accounts and devices. Subscribe to services to know your current exposure out on the internet and the dark web. Also limit what information you post on social media.
2FA/MFA
Utilizing some form or 2FA or MFA is paramount to keeping modern accounts and services secure. Hackers are counting on you to not use these methods. Just by enabling 2FA/MFA, you can block 100% of the automated bots, 96% of phishing attacks, and 76% of targeted attacks for most services. While this is an additional step to your login process, taking the additional 3-5 seconds to secure your account at login will ensure your accounts and privacy are safe. MFA is referred to as (i) something you know (e.g., password/personal identification number [PIN]); (ii) something you have (e.g., cryptographic identification device, token); or (iii) something you are (e.g., biometric).
Something you know:
Remembering all your passwords is extremely difficult especially if you have different ones for each service as recommended. Luckily there are password managers that help combat having to remember all those passwords. Applications such as Bitwarden provide a free service for securely storing and inputting your credentials on websites, services and apps. Bitwarden allows you to add their plugin on all major browsers as well as apps for mobile devices and is a must for anyone needing to access just about anything. These passwords will then sync between all devices. Bitwarden will also allow you generate random passwords based on your password requirements. Now there are other options for this out there but this will provide you with a great free option with very affordable paid options to expand on their free offerings. They also support a self-hosted “vault” for those who don’t trust the cloud offerings. Bitwarden has paid options which greatly expand upon their free tier especially for families or businesses needing to share credentials. Should you want to use more memorable passwords instead of randomly generated strings, I highly recommend using phrases or string of words. Examples of this can be I-Like-My-Passwords-Secure or MyPasswordisSuperSecure!. Avoid using words such as pets names, birthdays, or kids names which can easily be looked up via social engineering.
Something You Have:
Securing your account additionally from a secure password includes using a 2FA/MFA software or hardware token and SMS tokens. Popular software tokens include Google Authenticator, Authy and Microsoft Authenticator. Most services will allow these applications to generate a time based six-digit token that typically changes every 30-60 seconds. Most importantly these services will generate backup/recovery codes that should be stored in a physically secure location and not electronically. Should you loose access to your 2FA/MFA token, these recovery codes will allow you temporary access to your account and setup your authenticator of choice again.
Hardware tokens can also be utilized while being less common in the wild for regular users. Hardware tokens can be a battery powered device that generates a six-digit token every 30-60 seconds that you have on your person. These can easily attach on your keys. Another form of Hardware Token is a device such as a Yubi Key. Yubi keys are a hardware token you plugin to your devices and can have an additional authentication method such as biometrics.
Something You Are:
Physical devices such as Yubi Keys or hardware tokens with biometric scanners and other USB biometric scanners are a way to identify yourself physically satisfying the third method of MFA.
Monitoring Breaches:
Monitoring breaches has never been easier. One method for identifying if your account or password has been a part of breach is by visiting https://haveibeenpwned.com/. This site is run by a Microsoft security researcher who aggregates as many breaches as he can with almost 13B accounts currently listed. You can enter in your email address(s), passwords and phone number to see if you have been breached. You can also have the site notify you if your account comes up in any breaches.
Other services like Google will monitor your presence on the dark web as well as publicly available information on websites. Depending on the site, you can have Google request your removal of data from these sites. Google will not request your data be removed from public records or government sites. Google will notify you if your data shows up on the dark web so you can make changes to your accounts should your information be out there.
Anti-Virus and EDR software:
Anti-Virus or EDR software won’t keep your accounts from being breached per se but will help keep malware or credential stealing software off your computer. While there are free options out there, I do not recommend them by any means as they usually are behind with definition updates leading to potential attacks slipping through. Popular services include ESET, Bitdefender, CrowdStrike and SentinalOne to name a few. These will help protect you from common threats, potentially compromised websites, phishing emails and more.
VPN’s and Unsecure Networks:
Going to your favorite coffee shop and using their free WiFi isn’t all it may be cracked up to be. There is potential for someone to be there “sniffing” the wireless traffic waiting for some data to be transmitted that can easily be read or decoded. To combat this, only connect to secure networks minimally containing a password. Turn off your WiFi, Bluetooth and NFC connections when not in use. Hackers can fairly easily exploit these connections with fairly simple and inexpensive devices. When using the WiFi on a public network, use a VPN service such as Private Internet Access or NordVPN. These services will allow you to encrypt your traffic over the public network. This will assist you in preventing your data being transmitted and received on the wireless from being decrypted and used against you. Phones have hot spot options as well for a laptop to connect wirelessly via your phone using it’s cellular connection.
Social Media and You:
Social Media is the most used applications to date. We willing post so much information out on the internet and most times not even realizing what information we are posting. Did one of your friends post one of those questionaries about what’s your favorite color, your best friends name, year your graduated high school? Do these questions sound familiar? They should because you probably used them for password reset questions. Hacker’s love collecting social media posts and generating a profile on you. With enough information, hackers can pretend to be you and change your account information via a support call to major carriers and services. Be careful what you post out there. Even seemingly innocent posts such as pictures of your favorite things is enough for hackers to build their own profile on you. Be sure to review the information you post and who has access to seeing that information. Check your friends lists and make sure you know everyone. Even then, your friends and family accounts can be compromised. Best rule of thumb is that if you have even the slightest inkling that the message or post is sketchy or off from normal posts, it more than likely is an should not be interacted with.
Bonus Tip:
If you need to send someone a password, credit card number or any other sensitive information, please do not send it via email. Should your account get breached, hackers can search through and look for that information. Free services such as Password Pusher allow you to securely send credentials or any other text for free securely. You can limit the number of views and number of days the link is active for. You can even add an additional custom password that needs to be entered when opening the link.
Conclusion:
Hopefully you were able to learn some new ways to secure your accounts and keep yourself safe out on the internet. Should you wish for a security audit, recommendations on what you can be doing different or implementing these methods don’t hesitate to contact us. Either email us at daileycomputing@gmail.com or reach out via call or text to 203-693-1912. Also be sure to review our previous and future blog posts to keep you and your devices secure.


